- What's New
- Pricing & Purchasing
- Lead Times
- Literature & Samples
- Services & Warranties
- Careers
- Find a Rep
Explore Tributaire Cafe Tables

Inviting Connection
Tributaire café tables feature a graceful, fluid leg design that adds refinement and dash to cafés, communal areas, third spaces – anywhere people connect and renew their energies.
Key Features

Product Highlights

Sophisticated Finish Options

3 Heights, 3 Shapes
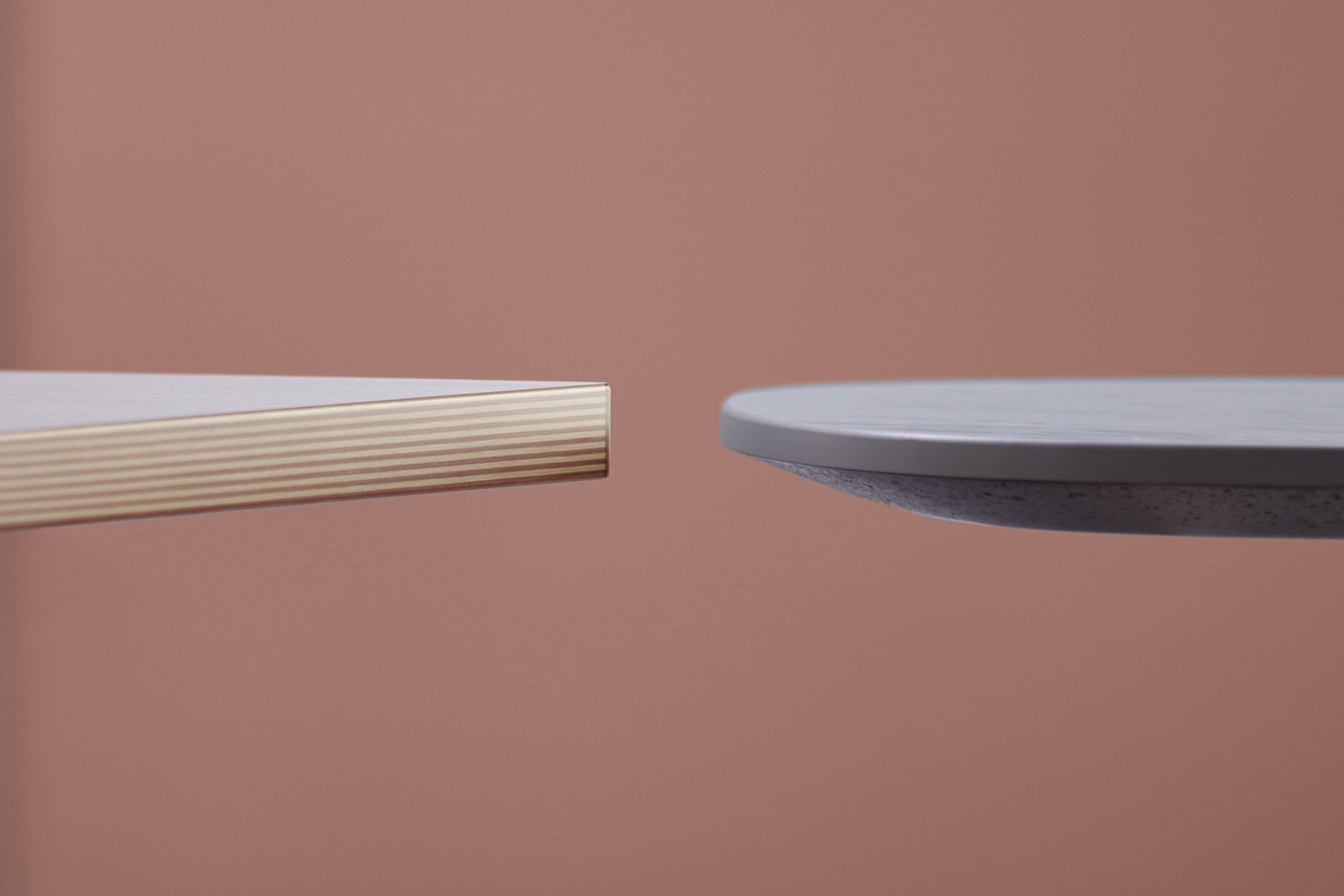
Elegant Edging
Complete Aesthetic Range

Tributaire Collection

List Price Starts At
$999 – $1,209
Lead Time
6* Weeks
*Chrome is 8 weeks.
Product Warranty
Lifetime






